Table of Content
- What is Networking?
- What is Internet
- Identify Devices on a Network
- MAC Addresses
- MAC Address Spoofing
- Ping (ICMP)
What is Networking?
Core Idea: Networking is about connections. It’s the principle of interconnected things, whether those things are people, systems, or devices.
Examples:
- Social: Friendship circles (shared interests, hobbies).
- Infrastructure: City transportation, national power grid, postal services.
- Neighborhood: Meeting and greeting neighbors.
- Computing: Interconnected technological devices (laptops, phones, security cameras, traffic lights, agricultural systems). This ranges from two devices to billions.
Significance:
Networks are fundamental to modern life, impacting everything from weather data collection to electricity distribution and traffic management. This pervasive nature makes understanding networking crucial for cybersecurity.
Key Points:
- Scalability: Networks can range from very small (two devices) to extremely large (billions of devices).
- Diversity: Networks connect diverse types of devices and systems.
- Real-world impact: Networks are deeply embedded in daily life.
- Cybersecurity relevance: Networking knowledge is essential for cybersecurity professionals.
What is Internet
Now we know what is network, just devices that connected each other. whats internet?
Internet is basically interconnection of small networks. network + network + network = Internet.”The Internet is one giant network that consists of many, many small networks within itself.”
The first iteration of the Internet was within the ARPANET project in the late 1960s. This project was funded by the United States Defence Department and was the first documented network in action. However, it wasn’t until 1989 when the Internet as we know it was invented by Tim Berners-Lee by the creation of the World Wide Web (WWW). It wasn’t until this point that the Internet started to be used as a repository for storing and sharing information, just like it is today.
Let’s relate Alice’s network of friends to computing devices. The Internet looks like a much larger version of this sort of diagram:

As previously stated, the Internet is made up of many small networks all joined together. These small networks are called private networks, where networks connecting these small networks are called public networks — or the Internet!
Questions
- Who invented the World Wide Web?
- Tim Berners-Lee
Identify Devices on a Network
To communicate on a network, there shud be a way to identify to whom im talking to. for that as humans we have name and fingerprints and for the devices when it comes to networking, they have IP addresses and MAC addresses.
- An IP Address
- A Media Access Control (MAC) Address — think of this as being similar to a serial number.
IP Addresses
Briefly, an IP address (or Internet Protocol) address can be used as a way of identifying a host on a network for a period of time, where that IP address can then be associated with another device without the IP address changing. First, let’s split up precisely what an IP address is in the diagram below:

An IP address is a set of numbers that are divided into four octets. The value of each octet will summarise to be the IP address of the device on the network. This number is calculated through a technique known as IP Addressing and Subnetting, but that is for another day. What’s important to understand here is that IP addresses can change from device to device but cannot be active simultaneously more than once within the same network.
IP Addresses follow a set of standards known as protocols. These protocols are the backbone of networking and force many devices to communicate in the same language, which is something that we’ll come onto another time. However, we should recall that devices can be on both a private and public network. Depending on where they are will determine what type of IP address they have: a public or private IP address.
A public address is used to identify the device on the Internet, whereas a private address is used to identify a device amongst other devices. Take the table & screenshot below as an example. Here we have two devices on a private network:
| Device Name | IP Address | IP Address Type |
|---|---|---|
| DESKTOP-KJE57FD | 192.168.1.77 | Private |
| DESKTOP-KJE57FD | 86.157.52.21 | Public |
| CMNatic-PC | 192.168.1.74 | Private |
| CMNatic-PC | 86.157.52.21 | Public |

These two devices will be able to use their private IP addresses to communicate with each other. However, any data sent to the Internet from either of these devices will be identified by the same public IP address. Public IP addresses are given by your Internet Service Provider (or ISP) at a monthly fee (your bill!)

As more and more devices become connected, it is becoming increasingly harder to get a public address that isn’t already in use. For example, Cisco, an industry giant in the world of networking, estimated that there would be approximately 50 billion devices connected on the Internet by the end of 2021. (Cisco., 2021). Enter IP address versions. So far, we have only discussed one version of the Internet Protocol addressing scheme known as IPv4, which uses a numbering system of 2^32 IP addresses (4.29 billion) — so you can see why there is such a shortage!
IPv6 is a new iteration of the Internet Protocol addressing scheme to help tackle this issue. Although it is seemingly more daunting, it boasts a few benefits:
- Supports up to 2^128 of IP addresses (340 trillion-plus), resolving the issues faced with IPv4
- More efficient due to new methodologies
The screenshot below compares both an IPv6 and IPv4 address.

MAC Addresses
MAC Address: A unique physical address assigned to a network interface card (NIC) at the factory. It’s a 12-character hexadecimal number (base-16) formatted as six pairs separated by colons (e.g., a4:c3:f0:85:ac:2d).
- Structure: The first six characters typically identify the manufacturer; the last six are a unique serial number.
MAC Address Spoofing
MAC Address Spoofing: The act of a device altering its MAC address to appear as another device. This exploits security systems relying on MAC address verification for access control.
Security Implications: Poorly designed security systems relying solely on MAC addresses for authentication are vulnerable to spoofing attacks. A common example is a firewall configured to trust specific MAC addresses. A spoofed MAC address could bypass such security measures.
Practical Applications: MAC address control is often used in public Wi-Fi networks (e.g., cafes, hotels) for:
- Access Control: Limiting access to authorized devices.
- Differentiated Services: Offering tiered service levels (e.g., faster speeds for a fee).
In short: While MAC addresses provide a unique physical identifier, their susceptibility to spoofing highlights the importance of robust security measures that extend beyond simple MAC address checks.
Ping (ICMP)
Ping is one of the most fundamental network tools available to us. Ping uses ICMP (Internet Control Message Protocol) packets to determine the performance of a connection between devices, for example, if the connection exists or is reliable.
The time taken for ICMP packets travelling between devices is measured by ping, such as in the screenshot below. This measuring is done using ICMP’s echo packet and then ICMP’s echo reply from the target device.
Pings can be performed against devices on a network, such as your home network or resources like websites. This tool can be easily used and comes installed on Operating Systems (OSs) such as Linux and Windows. The syntax to do a simple ping is ping IP address or website URL. Let’s see this in action in the screenshot below.
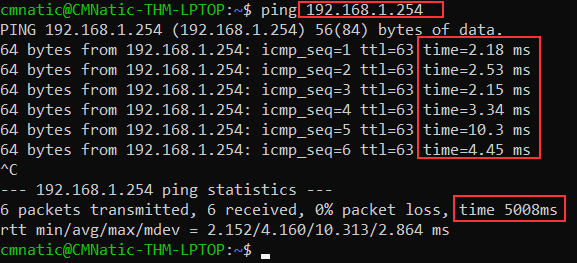
Here we are pinging a device that has the private address of 192.168.1.254. Ping informs us that we have sent six ICMP packets, all of which were received with an average time of 4.16 milliseconds.
Questions
- What protocol does ping use?
- ICMP ( Internet Control Message Protocol)
- What is the syntax to ping 10.10.10.10?
- ping 10.10.10.10
- What flag do you get when you ping 8.8.8.8?
- THM{I_PINGED_THE_SERVER}