Checking Hash Values of Pcap

 as md5 is not there i had to check manually :
as md5 is not there i had to check manually :
╰─❯ md5 xyz.pcap ─╯
MD5 (xyz.pcap) = 9981827f11968773ff815e39f5458ec8Network capture file details

Wireshark Endpoint Statistics
iPV4

Eth0 / Mac

Evidence
Evidence of searches conducted by user
GET /search?hl=en&q=i+want+to+harass+my+teacher HTTP/1.1\r\n

Suspect searched about vmware

Evidence of the search of “can i go to jail for harassing my teacher” and he accessed a virtual machine to do so

Evidence that jcoach switched to a windows virtual machine.

Find who sent email to lilytuckrige@yahoo.com and identify the TCP connections that include the hostile message

The packet n°80614 shows an harassing message was sent using sendanonymousemail.net
The source IP is 192.168.15.4, and the destination IP is 69.80.225.91
The packet n°83601 shows an harassing message was sent using Willselfdestruct.com, with the exact email header as described in the Powerpoint “you can’t find us”
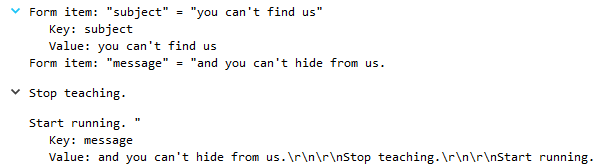
The source IP is 192.168.15.4, and the destination IP is 69.25.94.22
At this point of the article, we can confirm that the IP 192.168.15.4 plays a central role in the email “attacks” and the harassment faced by the professor Lily Tuckrige
| IP | MAC | Hardware |
|---|---|---|
| 192.168.15.4 (source) | 00:17:f2:e2:c0:ce | Apple |
Find information in one of those TCP connections that identifies the attacker
So now that we have an interesting IP / MAC pair, that may lead to the identification of the attacker, what could we do next ?
I’ve decided to have a look further in the packets. Could we find maybe, the email adress of the attacker ? And, how to check that ?
I’ve just filtered in Wireshark typing “frame contains mail”. This is a little bit “quick and dirty” but could help to narrow down the research as I had no better idea at this point…then I went scrolling into the selected frames and found some frames titled “GET /mail/ HTTP/1.1 with some interesting content…look at the cookie ! They reveal some email adress and the link to the email platform used !
In the example below, we see the frame n°16744, showing a GET /mail/ HTTP/1.1, the MAC adress in layer 2 of the OSI model, and some cookie informations in clear text :
User-Agent: Mozilla/5.0 (Macintosh; U; PPC Mac OS X Mach-O; en-US; rv:1.8.1.16)
Cookie pair: gmailchat=elishevet@gmail.com/945167
[Full request URI: http://mail.google.com/mail/]

gmailchat=elishevet@gmail.com/945167
Cookie pair: NID=8=PIHrm3_gKF3dFvrqD-o2IKj9qhB7at-vf-cHMDJsqV-Xk9jjDmnCcFgTaLXSA12hWxqIodI0DF5ODyrbV7gK1XLNz0vC3YGls9vpVe1U08b6o-gLp4Of5qxBiK--Exvf
Cookie pair: __utmz=173272373.1206412915.1.1.utmccn=(referral)|utmcsr=video.google.com|utmcct=/videouploadsuccess|utmcmd=referral
Cookie pair: PREF=ID=f374cfeeaf2ab8f5:TM=1178453904:LM=1202668046:GM=1:S=QZK9Q3YP8BqaQv6A
Cookie pair: rememberme=false
Cookie pair: __utma=173272373.1611040392.1206412915.1206412915.1206412915.1
\r\n
[Response in frame: 16746]
[Full request URI: http://mail.google.com/mail/]
Now that we have found a way to identify the email adress of the attacker, let’s go through the different frames including the GET /mail/ HTTP/1.1 info and let’s check the email, IP, MAC data. Probably, we will find a match with the already suspicious IP/MAC pair from the previous paragraph ? Here below the result of my analysis in a table, the match is easily found and highlighted in red
SO , i used ip.addr == 192.168.15.4 && frame contains “gmailchat” filter on wireshark, cuz we already know ip address 192.168.15.4 is the suspect and we found his gmail using this filter :


jcoachj@gmail.com Cookie pair: gmailchat=jcoachj@gmail.com/475090
NetworkMiner versus Wireshark
As we solved the case with Wireshark, let’s have a quick look what NetworkMiner could bring. Here a good summary available in Google

I will provide here below a few screenshots of what you can do to solve the case
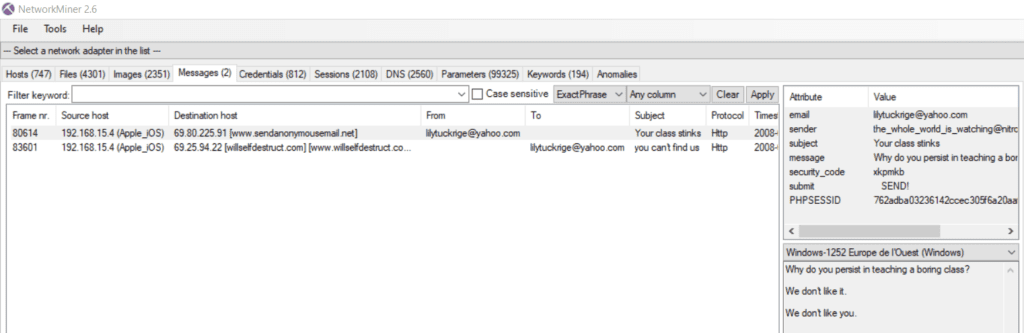
NetworkMiner provides a very handy email analyzer. We immediately see the harassment messages
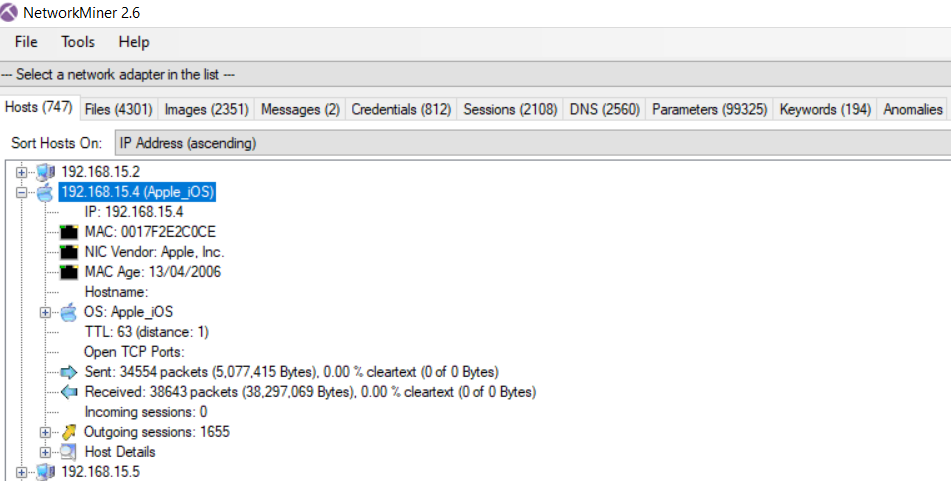
From the IP 192.168.15.4, we find the MAC adress and more
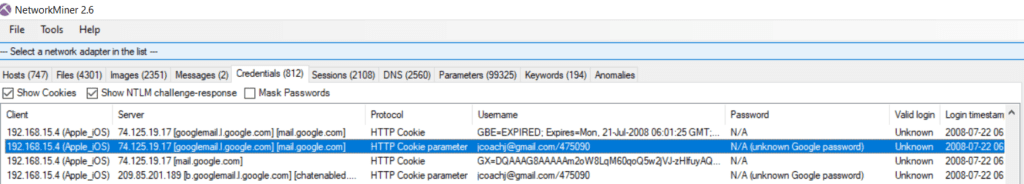
In the Credentials section, we can narrow down the email provider used by 192.168.15.4 to Gmail and confirm there is a single Gmail account corresponding to this IP, jcoach@gmail.com