SLIDES : HERE >>>
Public Key Infrastructure (PKI)
PKI is the backbone of secure online interactions. Think of it as a system for managing digital certificates, which are like digital IDs. These certificates rely on asymmetric cryptography – using a public key to encrypt data and a private key to decrypt it. The core components of PKI involve defining standards for public-key cryptography (we’ll see that in the next slide), establishing trust models (how we know a certificate is legitimate), and managing the entire lifecycle of these certificates. The time allocation here highlights the importance of this topic.
Public Key Infrastructure (PKI)
-
PKI is a framework for managing digital certificates.
-
Before PKI, managing digital certificates was chaotic. PKI provides a standardized framework for all the players involved: creating, storing, distributing, and revoking certificates. This standardized approach ensures consistency and reliability in digital certificate management.
-
Facilitates key management (creation, storage, distribution, revocation).
-
Uses Public-Key Cryptographic Standards (PKCS), defined by the RSA Corporation.
-
Trust Models in PKI
- Hierarchical Trust Model: A root CA issues certificates, but a single compromise can invalidate all.
- Distributed Trust Model: Multiple CAs sign certificates, reducing the risk of single-point failure.-
- Bridge Trust Model: A facilitator CA connects hierarchical and distributed models.
Public-Key Cryptographic Standards (PKCS)
PKCS are a series of standards, primarily defined by RSA Security (the creators of the RSA algorithm), that govern how PKI functions. They specify formats and procedures for various cryptographic operations. These standards are widely adopted and form the technical basis for many PKI implementations.
Trust models

Trust is fundamental to PKI. How do we know a certificate is authentic? That’s where trust models come in.
- Direct Trust: Simplest form; you personally know the other party. Limited scalability.
- Hierarchical Trust Model: Think of a tree structure. A root Certificate Authority (CA) – the top of the tree – issues certificates to subordinate CAs, who then issue certificates to individuals or organizations. This is efficient for managing certificates within a single organization. However, compromising the root CA’s key compromises the entire system.
- Distributed Trust Model: Multiple CAs operate independently, issuing certificates. More resilient than the hierarchical model because a single compromise doesn’t bring down the whole system.
- Bridge Trust Model: Acts as a connector between different hierarchical and distributed trust models. It doesn’t issue certificates itself, but facilitates trust relationships between otherwise separate PKI systems.
Managing PKI
Effective PKI management is critical. This involves two key documents:
- Certificate Policy (CP): A high-level set of rules defining how the PKI will operate, focusing on security requirements for CAs, Registration Authorities (RAs), and other components. It’s the “what” and “why”.
- Certificate Practice Statement (CPS): A detailed technical document outlining the procedures the CA uses for managing certificates – registration, issuance, revocation, key management. It’s the “how”.
Certificate Life Cycle
Certificates have a lifecycle: creation (after verification), suspension (temporary inactivity), revocation (permanently invalid), and expiration (end of validity).
Key Storage
Secure key storage is paramount. Public keys are often embedded within digital certificates. Private keys need more robust protection. Software-based storage is vulnerable; hardware solutions like smart cards and tokens offer better security.
Multiple key pairs can be used for enhanced security – one for encryption, one for signatures, keeping them isolated for better protection against compromise.
Key-Handling Procedures
This covers the various procedures around managing keys throughout their lifecycle:
- Key Escrow: A third party holds a copy of the key, typically split into parts for added security. Useful for recovery in emergencies.
- Expiration, Renewal, Revocation: Standard lifecycle events. Revocation is irreversible.
- Recovery: Procedures for regaining access to keys, possibly using a Key Recovery Agent (KRA) or multi-person authorization (M-of-N control).
- Suspension & Destruction: Temporary inactivation versus permanent removal.
Cryptographic Transport Protocols : SSL & TLS
-
Secure Sockets Layer (SSL)
- One of the most common transport algorithms
- Developed by Netscape
- Design goal was to create an encrypted data path between a client and a server
-
Transport Layer Security (TLS)
- Versions starting with v1.1 are significantly more secure than SSL v3.0
-
Cipher suite
- A named combination of the encryption, authentication, and message authentication code (MAC) algorithms that are used with SSL and TLS
-
Length of keys - a factor in determining the overall security of a transmission
- Keys of less than 2048 bits are considered weak
- Keys of 2048 bits are considered good
- Keys of 4096 bits are strong
-
Secure Shell (SSH)
- SSH is a secure alternative to Telnet, providing encrypted access to remote systems. It uses digital certificates for authentication and encrypts passwords.
- SSH is a suite for three utilities (slogin,ssh and scp)
- Using linux based CLI
- Client and server ends of the connection are authenticated using a digital certificate and passwords are encrypted
- Can be used as a tool for secure network backups
| Command | Description | Syntax | Secure Replacement |
|---|---|---|---|
rlogin | Log on to a remote computer | rlogin remotecomputer | slogin |
rcp | Copy files between remote computers | rcp [options] localfile remotecomputer:filename | scp |
rsh | Execute commands on a remote host without logging on | rsh remotecomputer command | ssh |
~ This table compares some old UNIX commands used for remote access and file transfer with their more secure replacements.
- HTTPS
- HTTPS is simply HTTP (the web protocol) running over SSL or TLS. It’s the “s” in “https://” that indicates the secure connection, using port 443 instead of HTTP’s port 80.
- IP Security (IPsec)
- IPsec is a suite of protocols for securing IP communications at the network layer. It provides authentication, confidentiality (encryption), and key management. It operates in two modes:
- Transport Mode: Only the data payload is encrypted.
- Tunnel Mode: Both the header and payload are encrypted.
- IPsec is a suite of protocols for securing IP communications at the network layer. It provides authentication, confidentiality (encryption), and key management. It operates in two modes:
Steganography
- Origin of the term: steganos: secret – graphy: writing
- The key difference: cryptography protects the content, steganography hides the existence of the content. They can be used together for stronger security.
- Uses of Steganography :
- Government
- Business : Digital Watermarking
- Individuals
Steg vs Cryptography
- Steganography and Cryptography are closely related
- The difference is in their goals :
- Cryptography: although encypted and unreadable, the existence of data is not hidden
- Steganography: no knowledge of the existence of the data
- Steganography and Cryptography can be used together to produce better protection
Digital Watermarking
A specific application of steganography, where information is embedded within a medium (often an image) to protect copyright or ownership. It’s designed to be difficult to remove without severely degrading the quality of the original.
Digital Steganography & Watermarking
- Digital watermarking hides data in a file, and the act of hiding data makes it a form or steganography
- The key difference is their goals :
- Steganography: hiding information
- Watermarking: extending the file with extra information
- Steganographic information must never be apparent to a viewer unaware of its presence.
Network Security and Steganography
- Confidentiality: any unauthorized person does not know that sensitive data exists
- Survivability: verifying that the data does not get destroyed in the transmission
- No detection: cannot be easily found out that the data is hidden in a given file
- Visibility: people cannot see any visible changes to the file in which the data is hidden
Types of Digital Steganography
- Hiding a Message inside Text
- Hiding a Message inside Images
- Most popular technique
- Hiding a Message inside Audio and Video Files
Hiding a Message inside Text
- Partially effective
randoM capitalosis is a rarE disEase ofTen contrAcTed by careless inTernet users. tHis sad illnEss causes the aFfected peRsON To randomly capitalize letters in a bOdy oF texT. please do not confuse this disease witH a blatant attEmpt aT steganogRAPhy.
Message is hidden in captial letters, when we put all captial letters together we can see the hidden message, this is not affective as much as it says
 Reveals: MEET AT THE FRONT OF THE TRAP
Reveals: MEET AT THE FRONT OF THE TRAP
More algorithms :
- First-letter algorithm
- Every n-th character
- Altering the amount of whitespace
- Using a publicly available cover source
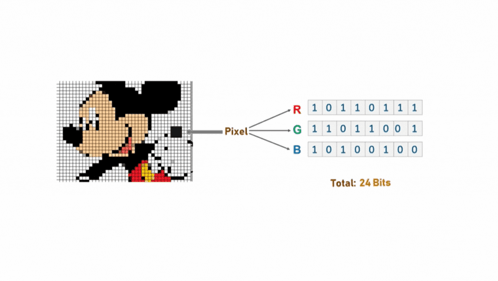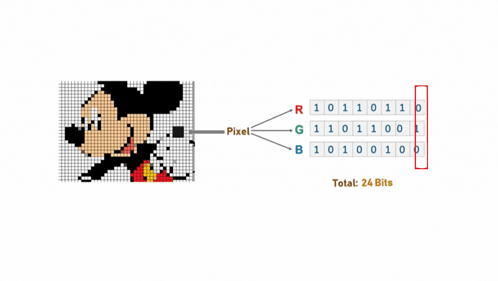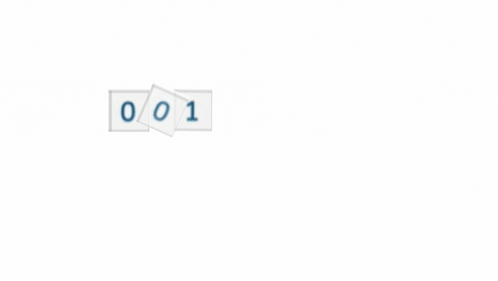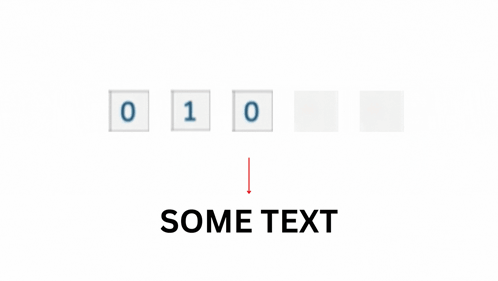
Hiding a Message inside Images
- The most popular medium!
- Least-significant bit (LSB) modifications
- 24-bit vs. 8-bit images
- Tools to implement LSB: EzStego and S-Tools
- Masking and Filtering
- Algorithms and Transformations
Hiding an Image within an Image
The least significant bit (LSB) modification is a popular method. 24-bit images offer more hiding capacity than 8-bit images. Tools like EzStego and S-Tools simplify this process. Masking and filtering can also be used.
Hiding a Message inside Audio or Video Files
- Advantages
- Human limitations – 20.000 Hz.
- Large amount of data that can be hidden inside
- Hard to recognize because of because of the continuous flow of information (moving stream of images and sound)
Steganalysis
- Detecting and decoding the hidden data within a given medium
- Even if secret content is not revealed, modifying the cover medium changes the medium’s statistical properties
- Distributed Dictionary Attack
Applications of Stegnography
| Application | Description |
|---|---|
| Combining explanatory information with an image | Used to embed additional information, such as doctor’s notes in an X-ray. |
| Embedding corrective audio or image data | Helps in restoring corrupted or degraded media due to poor transmission. |
| Peer-to-peer private communications | Enables users to exchange messages discreetly without attracting attention. |
| Posting secret communications on the web | Avoids direct transmission of confidential messages by embedding them in publicly accessible images or media. |
| Copyright detection | Embeds invisible watermarks in digital media to assert ownership rights. |
| Maintaining anonymity | Hides user identities by embedding messages in images, videos, or other files. |
| Hiding data on the network | Conceals sensitive data in case of a security breach, preventing easy detection. |
Steghide (CLI Tool)
- Able to hide data in various kinds of image- and audio-files.
- The color- respectively sample-frequencies are not changed thus making the embedding resistant against first-order statistical tests.
- Features
- compression of embedded data
- encryption of embedded data
- embedding of a checksum to verify the integrity of the extracted data
- support for JPEG, BMP, WAV and AU files
StegoSuite (GUI Tool)
- A free steganography tool written in Java.
- With Stegosuite, one can hide information in image files.
- Features
- BMP, GIF and JPG supported
- AES encryption of embedded data
- Automatic avoidance of homogenous areas (only embed data in noisy areas)
- Embed text messages and multiple files of any type
- Easy to use
Summary
This lesson explores steganography and its relationship to cryptography, focusing on how data can be hidden within various media types. While cryptography protects the content of a message by making it unreadable, steganography hides the existence of the message itself. Both techniques can be used together for enhanced security.
The lesson covers several key concepts:
-
Steganography Techniques: Various methods are described for embedding hidden information within different media: text (using techniques like altering capitalization or whitespace), images (primarily using Least Significant Bit – LSB – manipulation), and audio/video files (exploiting the limitations of human perception). Tools like Steghide (command-line) and StegoSuite (GUI) are mentioned.
-
Digital Watermarking: A specialized application of steganography used to assert ownership or copyright.
-
Steganalysis: The process of detecting and extracting hidden data. The lesson notes that even if the hidden data itself isn’t revealed, changes to the host medium’s statistical properties can indicate the presence of steganography.
-
Applications of Steganography: The lesson highlights diverse applications, ranging from embedding medical information within images to covert communication and copyright protection.
-
Steganography vs. Cryptography: The core difference is emphasized: cryptography makes data unreadable, while steganography conceals the data’s very existence. They are often used together for more robust security.
In essence, the lesson provides a comprehensive overview of steganography, its methods, tools, applications, and the challenges of both embedding and detecting hidden information.
