Table of Contents
- Learning Objectives
- Asymmetric Cryptography
- Using Cryptography
- Digital Signatures
- Digital Certificates
- Summary
SLIDES : HERE >>>
Learning Objectives
- List the various ways in which cryptography is used
- Define digital certificates
- List the various types of digital certificates and how they are used
Asymmetric Cryptography
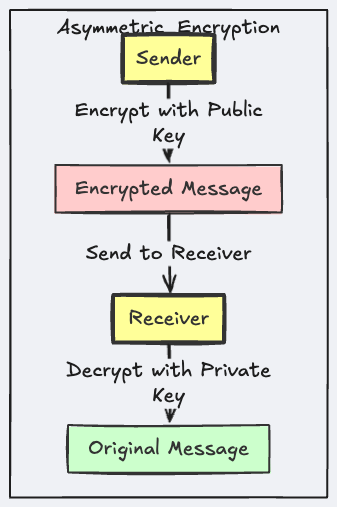 Unlike symmetric encryption, which uses the same key for both encryption and decryption, asymmetric encryption uses a pair of keys: one for encryption and another for decryption. This type of encryption is also known as public key cryptography.
Unlike symmetric encryption, which uses the same key for both encryption and decryption, asymmetric encryption uses a pair of keys: one for encryption and another for decryption. This type of encryption is also known as public key cryptography.
Encryption Process
- Data is encrypted using the public key. (mostly)
- The encrypted data can only be decrypted using the private key.
- The private key must be kept secure, while the public key is shared.
Detailed diagram

More about Asymmetric Encryption Cryptography Basics>>>
Key Exchange
- There are different solutions for a key exchange that occurs within the normal communications channel (in-band) of cryptography
- Diffie-Hellman (DH)
- Diffie-Hellman Ephemeral (DHE)
- Elliptic Curve Diffie-Hellman (ECDH)
- Perfect forward secrecy
Using Cryptography
- Should be used to secure data that needs to be protected.
- Can be applied through either software or hardware
Encrypt through Software
- File and file system cryptography
- Protecting groups of files through file system cryptography can be performed using
- Pretty Good Privacy (PGP)
- Widely used asymmetric cryptography system
- Used for files and e-mails on Windows systems
- GNU Privacy Guard (GPG)
- Runs on Windows, UNIX, and Linux operating systems
- Pretty Good Privacy (PGP)
- Microsoft Windows Encrypting File System (EFS)
- Whole disk encryption (bitlocker)
Hardware Encryption
- Software encryption can be subject to attacks to exploit or its vulnerabilities
- Hardware encryption options include :
- TPM Module (Trusted Platform Module)
- A chip on a computer’s motherboard that provides cryptographic services
- Includes a true random number generator
- Entirely done in hardware so it cannot be subject to software attack
- Prompts for password if hard drive moved to a new computer
- Prevents computer from booting if files or data have been altered
- Hardware Security Model
- A secure cryptographic processor
- Performs accelerated symmetric and asymmetric encryption
- Can provide services to multiple devices over a LAN
- TPM Module (Trusted Platform Module)
- USB Device Encryption
- Will not connect a computer until correct password has been provided
- All data copied to the drive is automatically encrypted
- Tamper-resistant external cases
- Administrators can remotely control and track activity on the devices
- Stolen drives can be remotely disabled
- Hard disk drive encryption
Digital Signatures
A digital signature is like an electronic seal or fingerprint that proves a message or document is authentic and unchanged.
🔹 How it works (simple steps): 1️⃣ The sender writes a message. 2️⃣ They use a secret code (private key) to create a unique signature for that message. 3️⃣ The receiver checks the signature using the sender’s public key to make sure it’s really from them and hasn’t been changed.
💡 Why use it? ✅ Ensures the message is from the real sender (authenticity) ✅ Confirms the message wasn’t altered (integrity) ✅ Prevents someone from denying they sent it (non-repudiation)
How Digital Signatures Work
- Signing: The sender uses their private key to create a digital signature for a message.
- Verification: The recipient obtains the sender’s public key from a trusted source. They use this public key to verify the signature. A successful verification confirms authenticity.
Normal Digital Signature Process

Attack: Fake Public Key Substitution
An attacker can deceive the recipient by substituting the legitimate public key with their own:
- Key Generation: The attacker creates a public-private key pair.
- Fake Message & Signature: The attacker crafts a fraudulent message and signs it using their private key.
- Verification with Fake Key: The recipient, unknowingly using the attacker’s public key, verifies the fraudulent signature. The verification succeeds, falsely confirming the message’s authenticity.
 Why This Works: Verification only confirms the signature matches the provided public key. If a fraudulent key is used, the system is tricked.
Why This Works: Verification only confirms the signature matches the provided public key. If a fraudulent key is used, the system is tricked.
Prevention:
The core vulnerability is trusting an untrusted source for the public key. Prevention strategies focus on ensuring key authenticity:
- Certificate Authorities (CAs): CAs vouch for the authenticity of public keys, issuing digital certificates.
- Multi-Channel Verification: Verify the public key directly with the sender before using it.
- Blockchain/Web of Trust: Decentralized systems offer alternative ways to establish trust and verify keys.
In short: Digital signatures are secure only if the public key used for verification is genuinely linked to the claimed sender. Without robust key authentication, the system is vulnerable to spoofing.
Digital Certificates
Trusted Third Party (TTP) & Digital Certificates
A Trusted Third Party (TTP) is an independent organization that helps verify identities and ensure the security of digital communications.
Key Functions of a TTP
-
Verifies Identity: Confirms that a public key truly belongs to a specific person or organization.
-
Prevents Impersonation Attacks: Stops attackers from pretending to be someone else by using a fake public key (Man-in-the-Middle Attack Prevention).
-
Issues Digital Certificates: Uses cryptographic techniques to link a public key to an individual or entity.
Digital Certificate & Digital Signatures
-
A Digital Certificate is an electronic document that proves a user’s identity and contains their public key.
-
It is digitally signed by a Trusted Third Party to ensure it is legitimate and hasn’t been altered.
How This Works in Security
-
A user requests a digital certificate from a trusted authority (e.g., Certificate Authority - CA).
-
The CA verifies the user’s identity and issues a certificate containing their public key.
-
Others can trust the public key by verifying the digital signature of the CA.
Why is This Important?
-
Ensures secure online transactions (e.g., SSL/TLS for websites).
-
Protects against identity spoofing in emails, documents, and secure systems.
-
Provides trust in digital communication.

Information contained in a digital certificate
- Owner’s name or alias
- Owner’s public key
- Issuer’s name
- Issuer’s digital signature
- Digital certificate’s serial number
- Expiration date of the public key
Managing Digital Certificates
Key Technologies for Managing Digital Certificates
Digital certificates are managed using several technologies that ensure their issuance, verification, and storage.
1. Certificate Authority (CA)
- Serves as a Trusted Third Party – Verifies identities and issues digital certificates.
- Responsible for Issuing Certificates – Confirms the identity of users, businesses, or websites before issuing certificates.
- Can Be Internal or External
- Internal CA: Managed within an organization for private use.
- External CA: Provided by trusted third-party organizations (e.g., DigiCert, Let’s Encrypt, GlobalSign).
2. Registration Authority (RA)
- Works as an intermediary between users and the CA.
- Validates identity before requesting the CA to issue a certificate.
- Ensures compliance with security policies before approving requests.
3. Certificate Repository (CR)
- A secure storage system for digital certificates.
- Allows users to retrieve, verify, and revoke certificates when needed.
- Helps ensure that only valid and trusted certificates are used.
Why is Digital Certificate Management Important?
-
Ensures trust and security in online communication.
-
Prevents impersonation and man-in-the-middle attacks.
-
Provides authentication and encryption for data protection.
Revocation & Status Verification
1. Certificate Revocation
- A process of invalidating a previously issued digital certificate before its expiration date.
- Once revoked, the certificate is no longer trusted.
Reasons for Certificate Revocation - Certificate is no longer used (e.g., the organization shuts down). - User’s details have changed (e.g., change in email, address, or job role). - Private key is lost or compromised (or suspected to be exposed).
2. Certificate Revocation List (CRL)
- A list of revoked certificates maintained by the Certificate Authority (CA).
- Contains serial numbers of revoked certificates.
- Published regularly but not updated in real-time.
- Can cause delays in checking certificate status.
3. Online Certificate Status Protocol (OCSP)
- Real-time lookup of a certificate’s status (faster than CRL).
- Uses a request-response model:
- The browser (or client) sends the certificate’s details to an OCSP Responder.
- The OCSP Responder checks the certificate’s status and returns one of three responses:
- Good – The certificate is valid.
- Revoked – The certificate has been revoked.
- Unknown – The status cannot be determined.
4. OCSP Stapling (Improved OCSP Process)
- A more efficient variation of OCSP used by web servers.
- The web server periodically queries the OCSP Responder and stores the signed, time-stamped response.
- When a client (browser) requests certificate status, the server provides the pre-fetched response, reducing load on the CA.
Benefits of OCSP Stapling:
- Faster verification (reduces network delays).
- More privacy-friendly (client doesn’t directly contact the CA).
- Reduces server load on OCSP responders.

Step-by-Step Explanation
-
Certificate Revocation List (CRL) Process
- CA maintains the CRL (list of revoked certificates).
- Browser requests the CRL from the CA.
- CA provides the CRL to the browser.
- Browser checks if the certificate is revoked.
- If revoked, the browser rejects the connection.
- If valid, the browser establishes a secure connection.
-
Online Certificate Status Protocol (OCSP) Process 7. Browser sends a request to the OCSP Responder to check certificate status. 8. OCSP Responder contacts the CA for the latest revocation information. 9. CA provides the certificate status (Good, Revoked, or Unknown). 10. OCSP Responder returns the status to the browser. 11. If revoked, the browser rejects the connection. 12. If valid, the browser establishes a secure connection.
-
OCSP Stapling (Faster Verification) 13. Web server periodically queries the OCSP Responder for certificate status. 14. OCSP Responder provides a signed, time-stamped response. 15. Web server sends the pre-fetched OCSP response when a browser requests the website. 16. Browser verifies the OCSP response and establishes a secure connection.
Summary
-
Asymmetric Cryptography: Uses public and private key pairs for encryption and decryption. The public key is widely shared, while the private key remains secret. Key exchange methods like Diffie-Hellman and its variants are discussed.
-
Cryptography Applications: Software-based encryption (PGP, GPG, EFS, BitLocker) and hardware-based encryption (TPM, hardware security modules, USB encryption, hard drive encryption) are detailed.
-
Digital Signatures: These provide authenticity, integrity, and non-repudiation. The sender signs a message with their private key, and the recipient verifies it using the sender’s public key. The document highlights a man-in-the-middle attack where a fake public key is substituted, compromising the system. Prevention strategies involve using Certificate Authorities (CAs), multi-channel key verification, and blockchain/web of trust models.
-
Digital Certificates: These are electronic documents that bind a public key to an identity, issued by a trusted third party (TTP), typically a Certificate Authority (CA). They are digitally signed by the CA to ensure authenticity. The document explains the roles of CAs, Registration Authorities (RAs), and Certificate Repositories (CRs) in managing digital certificates.
-
Certificate Revocation and Status Verification: Methods for revoking invalid certificates (CRL) and verifying their status in real-time (OCSP and OCSP stapling) are explained, highlighting the improvements in speed and efficiency offered by OCSP stapling. The process of certificate revocation and verification using both CRL and OCSP, including OCSP stapling, is detailed step-by-step.