SLIDES : HERE >>>
What is Cryptography?
- cryptography as a method to scramble data, making it unreadable to unauthorized individuals
- steganography, which hides data’s existence altogether.

Terms
- It explains the historical context (Caesar’s cipher) key terms like (origins of cryptography used by julius caesar)
- encryption (scrambling) : Change original text to cryptography (unreadable)
- decryption (unscrambling) : Changing Cryptography to cleartext
- cleartext (unencrypted data)
- plaintext (data to be encrypted)
- ciphertext (encrypted data)
- and the crucial role of the “key” in the cryptographic algorithm (the mathematical process).
Cryptography and Security
Cryptography can provide five basic protections
- Confidentiality
- Ensures only authorized parties can view it
- Integrity
- Ensures information is correct and unaltered
- Availability
- Ensures authorized users can access it
- Authentication
- Ensures sender can be verified through cryptography
- Non-repudiation
- Proves that a user performed an action
| Characteristic | Description | Protection |
|---|---|---|
| Confidentiality | Ensures that only authorized parties can view the information | Encrypted information can only be viewed by those who have been provided the key. |
| Integrity | Ensures that the information is correct and no unauthorized person or malicious software has altered that data | Encrypted information cannot be changed except by authorized users who have the key. |
| Availability | Ensures that data is accessible to authorized users | Authorized users are provided the decryption key to access the information. |
| Authentication | Provides proof of the genuineness of the user | Proof that the sender was legitimate and not an imposter can be obtained. |
| Non-repudiation | Proves that a user performed an action | Individuals are prevented from fraudulently denying that they were involved in a transaction. |
Cryptographic Algorithms
A fundamental difference in cryptographic algorithms is the amount of data processed at a time
- Stream cipher: takes one character and replaces it with another (encrypt one by one char)
- Block cipher : manipulates an entire block of plaintext at one time

- Sponge function: takes as input a string of any length and returns a string of any requested variable length
Categories of Cryptographic algorithms
- Hash algorithms
- Symmetric cryptographic algorithms
- Asymmetric cryptographic algorithms
Hash Algorithms
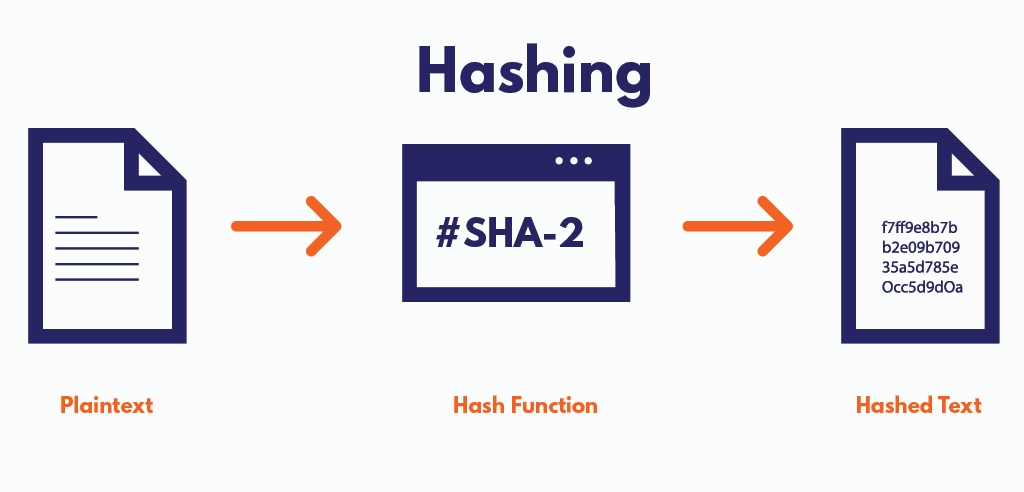 Hash algorithms generate fixed-size, unique “digital fingerprints” (digests) from input data. These digests are:
Hash algorithms generate fixed-size, unique “digital fingerprints” (digests) from input data. These digests are:
- Fixed-size: Always the same length, regardless of input size.
- Unique: Different inputs produce different digests. A tiny change in the input drastically alters the digest.
- Irreversible: The original data cannot be recovered from the digest.
Purpose: Hashing verifies data integrity. If a digest matches the expected value, it confirms the data hasn’t been altered.
HMAC (Hashed Message Authentication Code): Enhances security by incorporating a shared secret key into the hashing process. This prevents unauthorized modification and verification.
Popular Hash Algorithms:
- MD (Message Digest): Older algorithms (e.g., MD5) are now considered insecure due to collision vulnerabilities.
- SHA (Secure Hash Algorithm): A family of algorithms (e.g., SHA-256, SHA-512) offering varying levels of security. SHA-2 variants are currently widely used.
- Whirlpool: Designed for high security and considered robust.
- RIPEMD: Another family of algorithms (e.g., RIPEMD-160) offering strong collision resistance.
(Note: Specific strengths and weaknesses of each algorithm would require a more detailed explanation. For example, SHA-1 is deprecated due to collision vulnerabilities, while SHA-256 is currently considered secure.)
| Characteristic | Protection? |
|---|---|
| Confidentiality | No |
| Integrity | Yes |
| Availability | No |
| Authenticity | No |
| Nonrepudiation | No |
Comparing the popular hash algorithms mentioned is complex, as the “best” algorithm depends on the specific security requirements and application. However, we can compare them based on key characteristics:
| Feature | MD5 | SHA-1 | SHA-256 | SHA-512 | Whirlpool | RIPEMD-160 |
|---|---|---|---|---|---|---|
| Digest Size | 128 bits | 160 bits | 256 bits | 512 bits | 512 bits | 160 bits |
| Collision Resistance | Very Weak (broken) | Weak (broken) | Strong | Strong | Strong | Strong |
| Speed | Fast | Relatively Fast | Moderate | Slower | Moderate | Moderate |
| Security Level | Insecure | Insecure | Secure | Secure | Secure | Secure |
| Status | Deprecated | Deprecated | Widely Used | Widely Used | Used, but less common | Used, but less common |
Explanation of Columns:
-
Digest Size: The length of the hash output. Larger digest sizes generally offer better collision resistance.
-
Collision Resistance: This refers to the difficulty of finding two different inputs that produce the same hash. A “broken” algorithm means collisions have been practically demonstrated, rendering it insecure for cryptographic purposes.
-
Speed: The speed at which the algorithm computes the hash. Faster algorithms are generally preferable, provided they maintain sufficient security.
-
Security Level: A summary assessment based on collision resistance and known vulnerabilities.
-
Status: Indicates current usage and recommendation. MD5 and SHA-1 are deprecated and should not be used for security-sensitive applications.
Summary:
SHA-256 and SHA-512 are the current industry standards and are widely considered secure. Whirlpool and RIPEMD-160 also offer strong security, although they are less commonly used than SHA-2 variants. MD5 and SHA-1 are completely insecure and should be avoided. The choice between SHA-256 and SHA-512 often comes down to a balance between speed and security; SHA-512 offers slightly better security but is slower.
Symmetric Cryptographic Algorithms
 Definition: Symmetric cryptography uses the same secret key for both encryption and decryption. This is also known as private key cryptography because the key must be securely shared between communicating parties.
Definition: Symmetric cryptography uses the same secret key for both encryption and decryption. This is also known as private key cryptography because the key must be securely shared between communicating parties.
Key Characteristics:
- Single Key: One key is used for both encryption and decryption.
- Speed: Generally faster than asymmetric cryptography.
- Key Distribution: Secure key exchange is crucial; a compromised key compromises the entire system.
- Scalability: Key management becomes complex with a large number of participants. Each pair needs a unique secret key.
Popular Algorithms:
-
DES (Data Encryption Standard): An older algorithm now considered insecure due to its relatively short key size (56 bits). It’s largely deprecated.
-
3DES (Triple DES): Applies DES three times for enhanced security. While more secure than single DES, it’s slower and also being phased out in favor of AES.
-
AES (Advanced Encryption Standard): The current industry standard. Offers strong security with various key sizes (128, 192, and 256 bits). Widely used and considered secure for most applications.
-
Other Algorithms: RC4 (now considered insecure), IDEA, Blowfish.
-
One-Time Pad (OTP): Theoretically unbreakable if used correctly (a truly random key as long as the message, used only once). However, key distribution and management make it impractical for most real-world scenarios.
Strengths:
- High Speed: Efficient encryption and decryption.
- Simplicity: Relatively straightforward to implement.
Weaknesses:
- Key Distribution: Secure key exchange is a major challenge.
- Scalability: Managing keys becomes complex with many participants.
- Vulnerability to Key Compromise: If the key is compromised, all encrypted data is vulnerable.
Security Considerations: Choosing a strong algorithm (like AES with a sufficient key size) and implementing secure key management protocols are paramount for successful symmetric cryptography.
| Characteristic | Protection? |
|---|---|
| Confidentiality | Yes |
| Integrity | Yes |
| Availability | Yes |
| Authenticity | No |
| Nonrepudiation | No |
Classical Encryption Techniques
Substitution Cipher
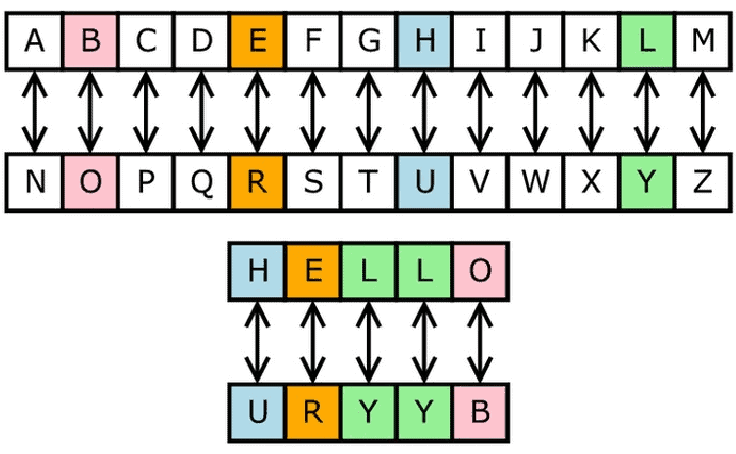 Definition: A substitution cipher replaces each character (or group of characters) in the plaintext with a corresponding character (or group) from a substitution alphabet. The core principle is to systematically map each element of the plaintext to a different element in the ciphertext.
Definition: A substitution cipher replaces each character (or group of characters) in the plaintext with a corresponding character (or group) from a substitution alphabet. The core principle is to systematically map each element of the plaintext to a different element in the ciphertext.
Mono-alphabetic Cipher

More About Mono-alphabetic Cipher >>> Monoalphabetic Substitution Cipher - A Detailed Explanation
Transposition Cipher
The cipher text is obtained by changing the column of the plaintext according to the alphabetic order of the letters of a key word.
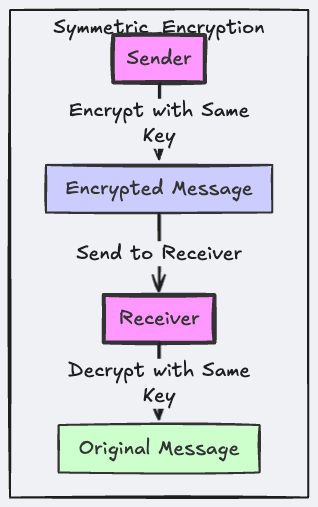
Symmetric Cryptography
- Uses one secret key for both encryption & decryption.
- Fast but requires secure key distribution.
Example Scenario
Suppose you have a password-protected document that you want to share with your colleague. You can email the encrypted document, but sending the password via email as well would be risky. If anyone gains access to your colleague’s email, they would have access to both the encrypted file and the password. Therefore, you must consider a different communication channel to securely share the password. One secure solution might be to meet in person and convey the password directly.
Symmetric Encryption Overview
- Same Key for Both Encryption and Decryption: The core idea of symmetric encryption is that both the sender and the recipient use the same key for encrypting and decrypting data.
- Challenges: The main difficulty in symmetric encryption is secure key distribution. If the key is intercepted, the entire encryption system becomes compromised.
Examples of symmetric encryption are DES (Data Encryption Standard), 3DES (Triple DES) and AES (Advanced Encryption Standard).
- DES was adopted as a standard in 1977 and uses a 56-bit key. With the advancement in computing power, in 1999, a DES key was successfully broken in less than 24 hours, motivating the shift to 3DES.
- 3DES is DES applied three times; consequently, the key size is 168 bits, though the effective security is 112 bits. 3DES was more of an ad-hoc solution when DES was no longer considered secure. 3DES was deprecated in 2019 and should be replaced by AES; however, it may still be found in some legacy systems.
- AES was adopted as a standard in 2001. Its key size can be 128, 192, or 256 bits.
There are many more symmetric encryption ciphers used in various applications; however, they have not been adopted as standards.
Asymmetric Cryptographic Algorithms
 Unlike symmetric encryption, which uses the same key for both encryption and decryption, asymmetric encryption uses a pair of keys: one for encryption and another for decryption. This type of encryption is also known as public key cryptography.
Unlike symmetric encryption, which uses the same key for both encryption and decryption, asymmetric encryption uses a pair of keys: one for encryption and another for decryption. This type of encryption is also known as public key cryptography.
Encryption Process
- Data is encrypted using the public key. (mostly)
- The encrypted data can only be decrypted using the private key.
- The private key must be kept secure, while the public key is shared.
Key Examples
- RSA: Commonly uses 2048-bit, 3072-bit, or 4096-bit keys.
- Diffie-Hellman: Uses similar key sizes to RSA (e.g., 2048-bit minimum, with higher keys for added security).
- Elliptic Curve Cryptography (ECC): Uses shorter keys for the same security as RSA. For example, a 256-bit ECC key is comparable in security to a 3072-bit RSA key.
Asymmetric Scenario
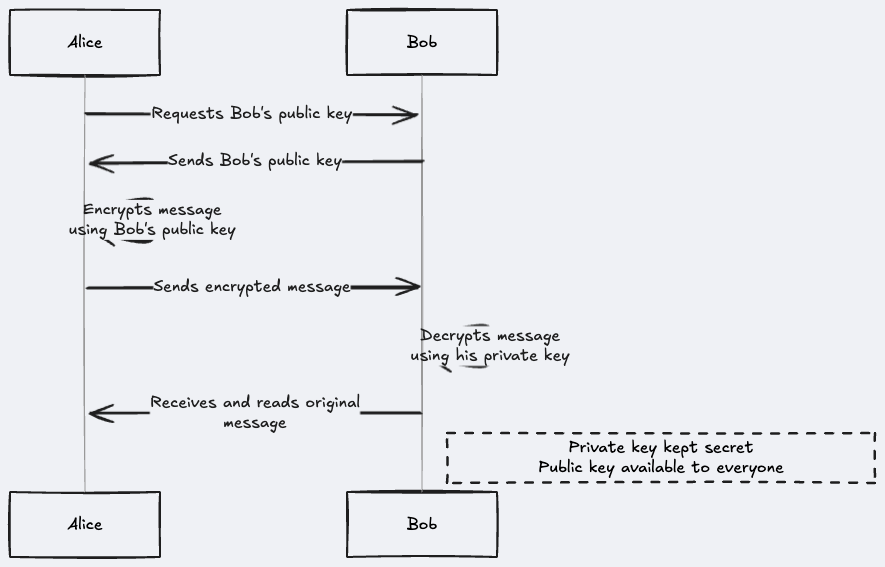
Scenario: Secure Messaging with Asymmetric Encryption
Alice wants to send a secret message to Bob, ensuring only Bob can read it. This is how asymmetric encryption (also known as public-key cryptography) makes it possible:
-
Key Generation: Bob generates a pair of keys: a public key and a private key. The public key can be freely shared, while the private key must remain secret. Think of it like a mailbox: everyone (including Alice) can drop a letter into the mailbox (public key), but only Bob has the key to open it (private key).
-
Public Key Distribution: Bob makes his public key available to Alice (e.g., through a website, certificate, or secure channel).
-
Encryption: Alice obtains Bob’s public key. She uses this key to encrypt her message. This is represented by the “Encryption with Alice’s Public Key” box in the diagram. Only Bob’s private key can decrypt the message.
-
Transmission: Alice sends the encrypted message to Bob. Even if someone intercepts the message during transmission, they cannot decrypt it without Bob’s private key.
-
Decryption: Bob receives the encrypted message. He uses his private key (which he keeps secret) to decrypt it, retrieving the original message. This is represented by the “Decryption with Alice’s Private Key” box.
Why Only Bob Can Decrypt: The mathematical properties of asymmetric encryption algorithms ensure that decrypting the message is computationally infeasible without the corresponding private key, even if you have the public key.
Answer to your question: Anyone can encrypt a message using Bob’s public key, but only Bob can decrypt it using his private key. The security relies on keeping the private key secret.
Summary
This note provides an overview of cryptography, focusing on its principles, algorithms, and applications. It begins by defining cryptography and steganography, introducing key terminology (encryption, decryption, plaintext, ciphertext, key). The five basic security services provided by cryptography are explained: confidentiality, integrity, availability, authentication, and non-repudiation.
The core of the note delves into different types of cryptographic algorithms:
-
Hash Algorithms: These create fixed-size, unique “digital fingerprints” (digests) of data, used for verifying data integrity. Several algorithms are compared (MD5, SHA-1, SHA-256, SHA-512, Whirlpool, RIPEMD-160), highlighting the deprecation of MD5 and SHA-1 due to vulnerabilities. SHA-256 and SHA-512 are presented as current secure standards.
-
Symmetric Cryptographic Algorithms: These use the same secret key for encryption and decryption. Algorithms like DES (deprecated), 3DES (deprecated), and AES (current standard) are discussed, emphasizing the challenge of secure key distribution.
-
Asymmetric Cryptographic Algorithms (Public Key Cryptography): These utilize a pair of keys (public and private) for encryption and decryption. The public key is widely shared, while the private key must remain secret. RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC) are mentioned as examples. A scenario illustrating secure messaging using asymmetric encryption is provided.
The note also covers classical encryption techniques like substitution (monoalphabetic) and transposition ciphers. Finally, it contrasts symmetric and asymmetric cryptography, detailing their strengths, weaknesses, and use cases, with examples illustrating secure key exchange challenges in symmetric systems and secure communication using public key cryptography.