SLIDES : Here >>>

Objectives
- List and explain different server-side web application attacks: We’ll look at how attackers target the servers running web applications.
- Define client-side attacks: Here we’ll explore attacks that target the user’s computer or browser directly.
- Explain how overflow attacks work: Although not detailed in this specific presentation, understanding the principle of overflow attacks is essential for network security.
- List different types of networking-based attacks: We’ll examine attacks that target the network infrastructure itself.
Application Attacks
Application attacks can target the server, the client (the user’s computer), or both. Think of it like this: the application is a house. You can attack the house itself (server), the people inside (client), or both.

Server-Side Web Application Attacks
Protecting server-side applications is often harder than protecting other systems. Traditional firewalls and network security tools often miss web application attacks because they focus on network traffic, not the content of that traffic (what’s actually in the data being sent).
A “zero-day attack” is a particularly nasty type – it exploits a brand new vulnerability that nobody knows about yet, so there’s no defense in place.
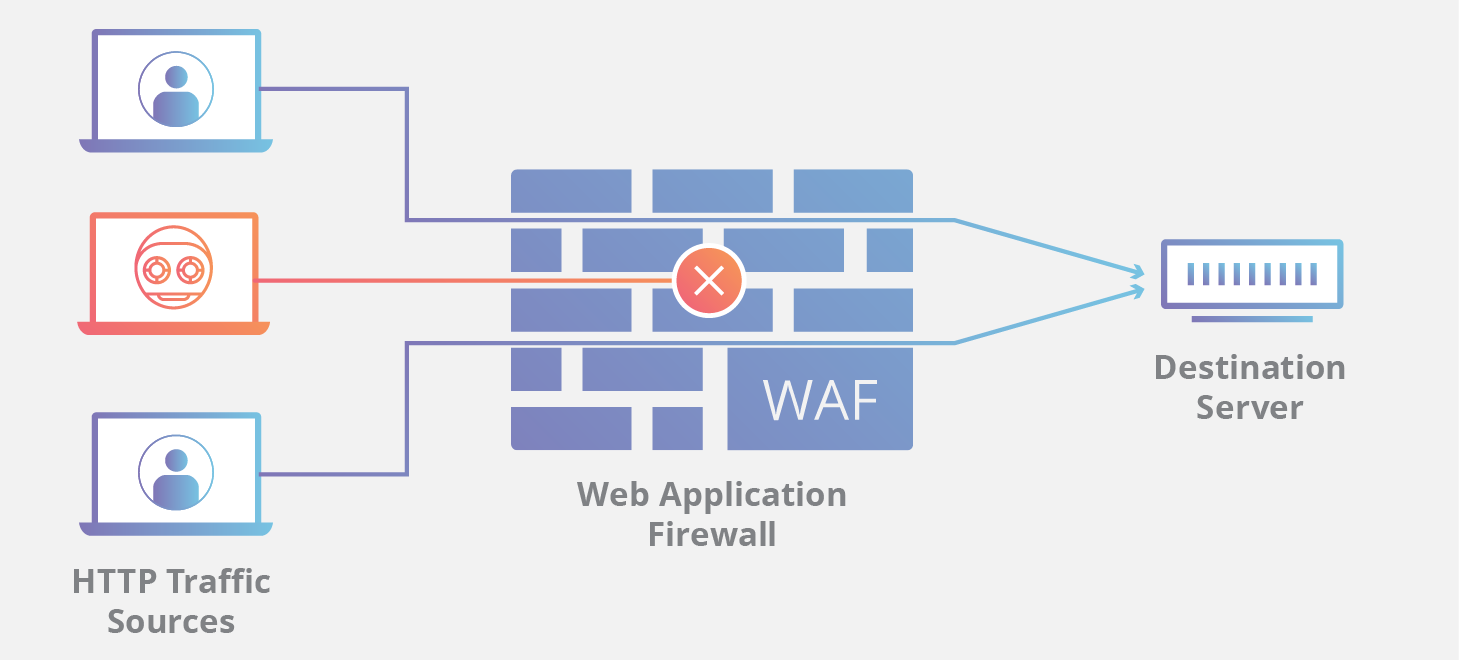
Many server-side attacks involve manipulating the input a web application receives from users. We’ll focus on three common ones:
- Cross-site scripting (XSS): Injecting malicious scripts into a website.
- SQL injection: Injecting malicious SQL commands into database queries.
- XML injection: Injecting malicious XML code. (Command injection/directory traversal are mentioned but out of scope for this session.)
EXTRA KNOWLEDGE
- Directory traversal, also known as path traversal, is a type of web security vulnerability that allows an attacker to access directories and files that are stored outside the web root directory. This vulnerability occurs when user input is not properly sanitized, allowing an attacker to manipulate file paths and gain unauthorized access to restricted files.
- Command Injection is a critical security vulnerability that occurs when an attacker can execute arbitrary system commands on a server or host machine through a vulnerable application. This happens when the application improperly handles user input and passes it to system-level commands without adequate validation or sanitization.
Cross Site Scripting XSS
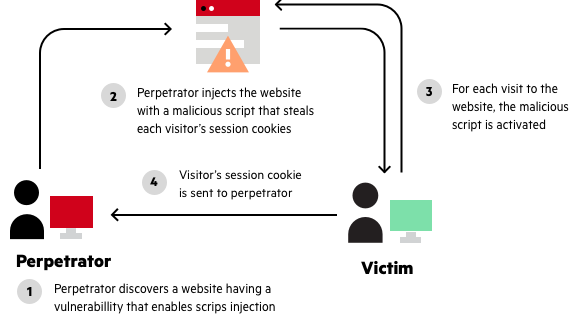
XSS involves injecting malicious scripts into a web application. When a victim visits the compromised website, their browser executes the malicious script, potentially stealing their information or performing other harmful actions.
A vulnerable website typically:
- accepts user input without proper validation, and
- uses that input directly in its responses, without sanitizing it.
Types of XSS:
-
Reflected XSS: This is like writing a malicious message on the board, and then sending a link to someone else. When they click the link, your malicious message appears on the board, and their browser executes it. It’s reflected back to the victim from the server. The attack is temporary; the malicious code isn’t saved on the website.
-
Stored XSS (Persistent XSS): This is like writing a malicious message on the board and leaving it there permanently. Anyone who visits the board and reads that message will have their browser execute the malicious code. The attack is persistent; the malicious code is stored on the website’s server.
-
DOM XSS: This is like changing the behavior of the message board itself. Instead of directly writing a message, you manipulate the website’s code (Document Object Model) in the user’s browser, making it do something malicious. This happens entirely within the victim’s browser, without the malicious code ever being sent to or stored on the server.
More into XSS >
SQL Injection
SQL injection attacks target databases by injecting malicious SQL code into user inputs. The example given shows how an attacker might try to retrieve all email addresses from a database by manipulating a password recovery form. The attacker tries to exploit poor input validation.
https://tryhackme.com/r/room/sqlinjectionlm
https://youtube.com/shorts/_ZCv6fROPTg?si=cvFA1lvzuiSb9-6x
XML vs HTML
XML (Extensible Markup Language) and HTML (HyperText Markup Language) are both markup languages used to structure data, but they serve different purposes and have key distinctions:
HTML (HyperText Markup Language):
-
Purpose: Primarily used for displaying content on web pages. It defines the structure and presentation of text, images, videos, and other elements within a web browser. It focuses on how information looks.
-
Structure: Uses predefined tags (like
<p>,<h1>,<img>, etc.) to represent elements. The structure is relatively fixed and follows a standard set of rules. Browsers understand these tags and render the content accordingly. -
Flexibility: While HTML allows for some degree of styling through CSS and some dynamic content through JavaScript, its main purpose is static content presentation.
XML (Extensible Markup Language):
-
Purpose: Designed for storing and transporting data. It’s not directly rendered by a browser in the same way as HTML. Instead, it focuses on what the data is, independent of how it’s displayed. It’s used to structure and organize data for various applications and systems.
-
Structure: Uses custom tags defined by the user or application. This makes it highly flexible and adaptable to different data structures. You can create tags that accurately represent your specific data fields.
-
Flexibility: Its key strength lies in its flexibility. You can define your own tags to represent any type of data, making it ideal for data exchange between different systems and applications.
Key Differences Summarized:
| Feature | HTML | XML |
|---|---|---|
| Purpose | Displaying web content | Storing and transporting data |
| Tags | Predefined tags | User-defined tags |
| Rendering | Directly rendered by web browsers | Not directly rendered; processed by apps |
| Flexibility | Limited for data representation | Highly flexible for data representation |
| Focus | Presentation | Data structure and content |
Analogy:
Think of HTML as a beautifully designed brochure – it’s focused on visually presenting information in an appealing way. XML, on the other hand, is like a well-organized database – it’s focused on efficiently storing and managing data regardless of how it looks. You might use XML to store the data that then gets displayed using HTML.
Client-Side Application
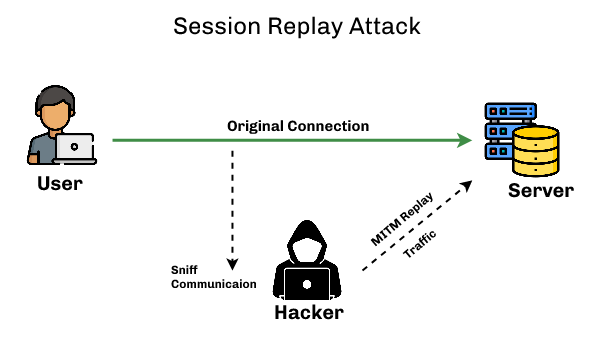
Unlike server-side attacks, client-side attacks target vulnerabilities in the user’s browser or applications. The client initiates the connection to the server, but malicious code on the server can compromise the client.
- Drive-by downloads: The user’s computer is infected simply by visiting a compromised website (often through invisible iframes).
- Header manipulation: Attackers modify HTTP headers (like the “Referer” or “Accept-Language” headers) to perform malicious actions or hide their tracks.
- Cookies: Small pieces of data stored on the user’s computer; they can be exploited by attackers. The slide differentiates between first-party, third-party, session, and persistent cookies.
- Locally Shared Objects (LSOs): Also known as Flash cookies, these store more data than regular cookies and pose similar risks.
- Malicious attachments: Emails with infected files are a common attack vector.
- Session hijacking: Attackers steal or guess a user’s session token to impersonate them.
References >>
- Malicious Add-Ons : Browser add-ons or extensions can be malicious and used to compromise the user’s system, often by exploiting vulnerabilities in technologies like ActiveX.
- Networking Based Attacks : Attacks targeting network infrastructure can affect many devices simultaneously. The slide lists several types: Denial of Service, Interception, Poisoning, and Attacks on Access Rights.
Denial of Service DoS

DoS (Denial of service == Unavailability of the service) attacks flood a system with requests, making it unavailable to legitimate users. DDoS (Distributed Denial of Service) uses many compromised computers (a botnet) to amplify the attack. Specific examples given are Ping floods, Smurf attacks, and SYN floods.
Interception
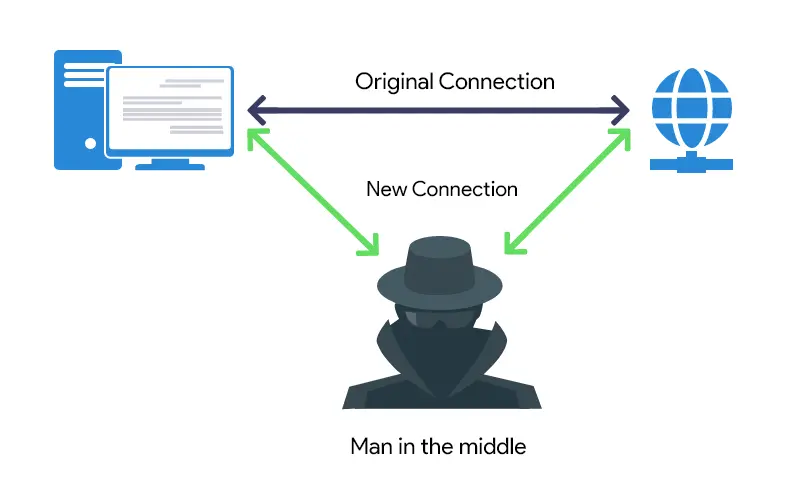 Man-in-the-middle attacks intercept communication between two parties. Passive attacks only observe, while active attacks modify the communication.
Man-in-the-middle attacks intercept communication between two parties. Passive attacks only observe, while active attacks modify the communication.
More about MITM >> : Man-in-the-Middle Attack MITM
DDOS
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of internet traffic. Unlike a Denial-of-Service (DoS) attack, which originates from a single source, a DDoS attack uses multiple compromised computer systems, often called a botnet, as sources of the attack traffic.
DoS vs DDOS
| Feature | DoS (Denial of Service) | DDoS (Distributed Denial of Service) |
|---|---|---|
| Source | Single source (one computer or device) | Multiple sources (a botnet of compromised computers) |
| Scale | Relatively small-scale attack | Large-scale attack, potentially massive bandwidth |
| Complexity | Easier to launch | More complex to launch and maintain a botnet |
| Detection | Easier to detect (often originates from one IP) | Harder to detect due to distributed nature of attacks |
| Mitigation | Often manageable with basic security measures | Requires more advanced and sophisticated mitigation |
| Impact | Can disrupt service but often temporary | Can cause significant and prolonged service outages |
| Techniques | Ping floods, SYN floods, UDP floods, etc. | Same techniques as DoS, but amplified by botnet |
| Target | Single server or network | Single server or network, or entire network segments |
Poisoning
Poisoning attacks inject false information into network processes. ARP poisoning modifies the Address Resolution Protocol table, while DNS poisoning modifies the Domain Name System records.
References >>