What is Active Directory (AD)?
Active Directory (AD) is a system used in Windows networks to manage everything centrally. This includes users, computers, groups, and other resources like file shares and devices. It helps organize and control who can access what in a network.
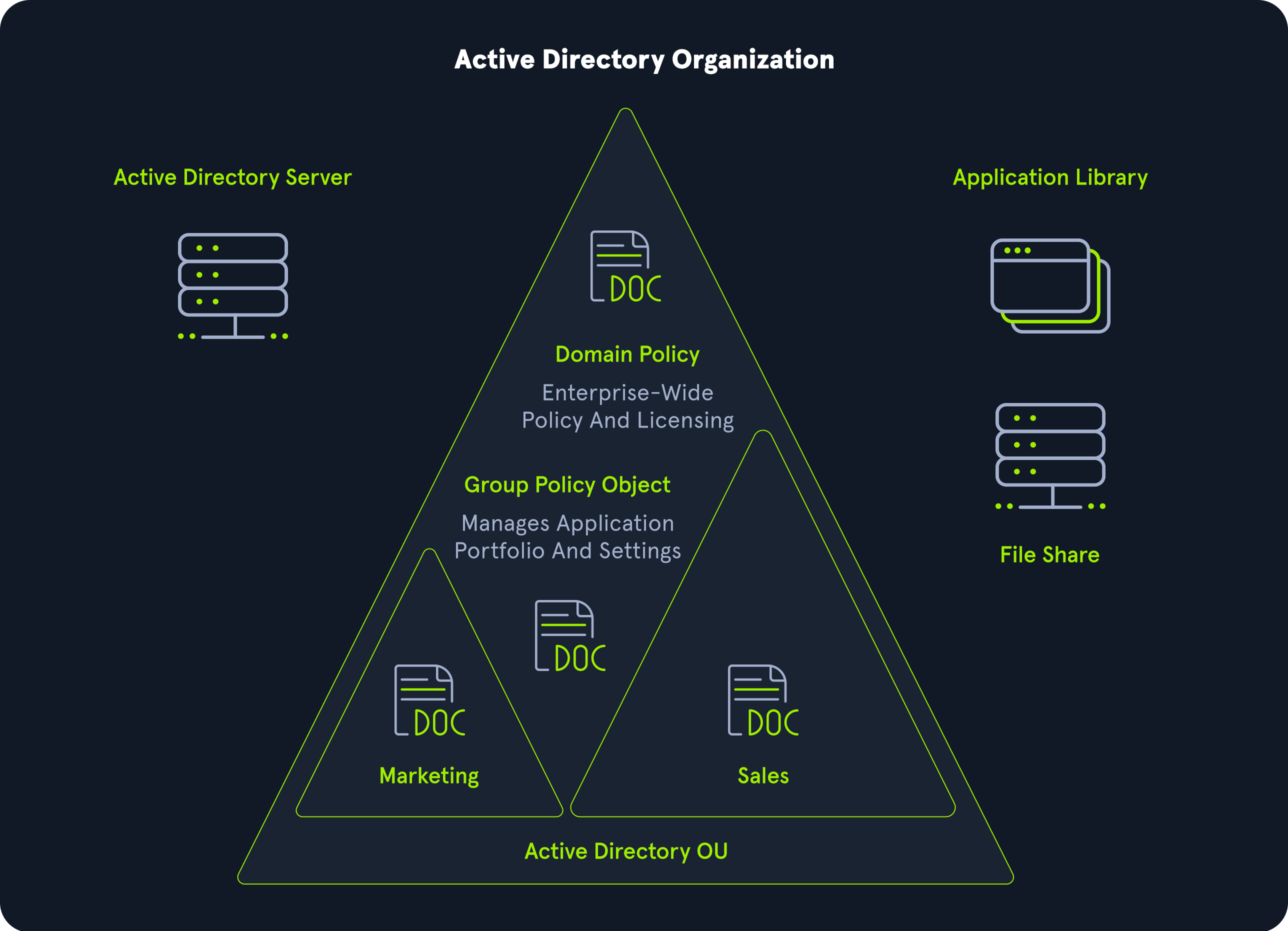
Key Features of AD
- Centralized Management: Makes it easier for administrators to control resources in one place.
- Authentication & Authorization: Ensures only authorized users can access resources.
- Scalability: Can handle millions of objects and grow with an organization.
Why is AD Vulnerable?
- Not Always Secure by Default: Some settings aren’t automatically secure, leaving room for mistakes.
- Easy to Misconfigure: A single misstep can create weaknesses in the system.
- Accessible to All Users: Even regular users can view a lot of information about the network.
- Attack Risk: Misconfigurations can allow attackers to move around the network and gain unauthorized access.
Why is AD Vulnerable?
- Not Always Secure by Default: Some settings aren’t automatically secure, leaving room for mistakes.
- Easy to Misconfigure: A single misstep can create weaknesses in the system.
- Accessible to All Users: Even regular users can view a lot of information about the network.
- Attack Risk: Misconfigurations can allow attackers to move around the network and gain unauthorized access.
Why Understanding Active Directory (AD) Matters
Importance of AD in Organizations
 Active Directory is critical for managing networks, and around 95% of Fortune 500 companies rely on it. This makes it a prime target for attackers. If a malicious actor gains access to AD as a standard user (e.g., through phishing), they can start exploring the network to find weak points and plan further attacks.
Active Directory is critical for managing networks, and around 95% of Fortune 500 companies rely on it. This makes it a prime target for attackers. If a malicious actor gains access to AD as a standard user (e.g., through phishing), they can start exploring the network to find weak points and plan further attacks.
Fortune 500?
The Fortune 500 is a yearly list of the 500 largest companies in the U.S. based on their total revenue.
Key Attack Examples
-
Ransomware Focus on AD:
- Attackers, such as the Conti ransomware group, target AD because it gives them control over the entire network.
- They exploit vulnerabilities like:
- PrintNightmare (CVE-2021-34527): A flaw in the Windows Print Spooler service
- Zerologon (CVE-2020-1472): A critical vulnerability in the Netlogon protocol.
- These allow attackers to escalate privileges and move freely across the network.
-
Simple Access, Big Damage:
- Even basic domain users can sometimes find and exploit flaws in AD to gain administrative control.
Why Learn AD as a Security Professional?
-
Encounter AD Frequently: AD is a common part of many networks, so understanding it is essential for both offense (attacks) and defense (protection).
-
Prevent Future Attacks:
- By studying AD structure and vulnerabilities, we can:
- Detect flaws before attackers do.
- Strengthen defenses against ransomware and other threats.
- By studying AD structure and vulnerabilities, we can:
-
Effectiveness of Tools:
- Many tools exist to test AD security (e.g., for penetration testing).
- However, tools are only as good as the person using them. Understanding AD is crucial to make the most of these tools.
What This Module Will Cover
-
AD Structure and Function:
- Learn how AD works, including its objects and permissions.
-
User Rights and Privileges:
- Understand the roles and permissions within an AD environment.
-
Tools and Processes:
- Explore tools and methods to manage, test, and secure AD.
-
Practical Examples:
- Walkthroughs of setting up and managing a small AD environment.
History of Active Directory
https://arc.net/l/quote/rfbxnife
Active Directory’s roots trace back to LDAP (Lightweight Directory Access Protocol), first introduced in RFCs as early as 1971. The X.500 organizational unit concept, a precursor to modern directory systems, emerged in 1993 with Novell Directory Services.
While Microsoft initially attempted directory services with Windows NT 3.0 (1990), incorporating LAN Manager and OS/2 elements, Active Directory’s true genesis lies in the mid-1990s. It wasn’t integrated into the Windows operating system until Windows Server 2000. A beta release appeared in 1997.
Key Milestones
- 1971: LDAP foundational RFCs released.
- 1990: Windows NT 3.0 attempts directory services.
- 1993: Novell Directory Services introduces X.500-based organizational units.
- Mid-1990s: Active Directory development begins.
- 1997: Active Directory beta release.
- 2000: Active Directory integrated into Windows Server 2000.
- 2003: Windows Server 2003 introduces Forests (containers for domains, users, etc.).
- 2008: Windows Server 2008 introduces Active Directory Federation Services (ADFS) for Single Sign-On (SSO).
- 2016: Windows Server 2016 enhances cloud migration capabilities, adds security features like Group Managed Service Accounts (gMSA) to mitigate Kerberoasting, and releases Azure AD Connect for Office 365 integration.
Timeline Visualization
timeline
title Active Directory Timeline
1971 : LDAP RFCs
1990 : Windows NT 3.0 (early directory services)
1993 : X.500 & Novell Directory Services
1997 : Active Directory Beta
2000 : Active Directory in Windows Server 2000
2003 : Forests introduced (Windows Server 2003)
2008 : ADFS introduced (Windows Server 2008)
2016 : Cloud migration focus, gMSA, Azure AD Connect (Windows Server 2016)
Ongoing Evolution and Vulnerabilities
Active Directory has continuously evolved, but it has also been plagued by misconfigurations and vulnerabilities since its inception. New flaws are regularly discovered, highlighting the ongoing need for patching and robust security practices. This makes understanding AD crucial for both security professionals (for defense) and penetration testers (for offense). The near-ubiquitous nature of AD in enterprise environments (95% of Fortune 500 companies) emphasizes its importance as a target and a critical area of security focus.